WireGuard

I always used OpenVPN in my servers, but now WireGuard is a better option:
- It’s simpler
- It’s more efficient
- It’s faster
- It uses modern cryptography algorithms
I’m using it to remotely access private services in my home server. I setup a star topology, where all the VPN clients connect to the home server and they can only see the server.
So I need a dynamic DNS and an open port in the router, I already have them for Home Assistant.
Eloy Coto recommended Tailscale, it is an amazing mesh VPN based in WireGuard. It’s much simpler to set up, and you do not need to open public ports, but it’s commercial and a bit overkill for my needs.
Generating the WireGuard configurations
The most tedious part of WireGuard is to generate the configurations, but there are some nice tools to ease that, like:
https://www.wireguardconfig.com/
The tool generates the configuration for the server and for the requested number of clients. It does everything in the frontend, so it is not leaking the VPN keys.
As I’m only acessing the server, I have removed the IP forwarding options in the Post-Up and Post-Down rules.
Installing and configuring the WireGuard server
WireGuard is in the official Ubuntu repos, so to install it in the server it’s enough to do:
sudo apt install wireguardThen I needed to put the config in the /etc/wireguard/wg0.conf file and do:
sudo systemctl enable wg-quick@wg0.service
sudo systemctl start wg-quick@wg0.serviceInstalling and configuring the clients
WireGuard has clients for almost any OS:
https://www.wireguard.com/install/
To setup the client in the phones, the WireGuard Config web tool generates QR codes. In other devices you’ll need to create a file with it or paste the config contents.
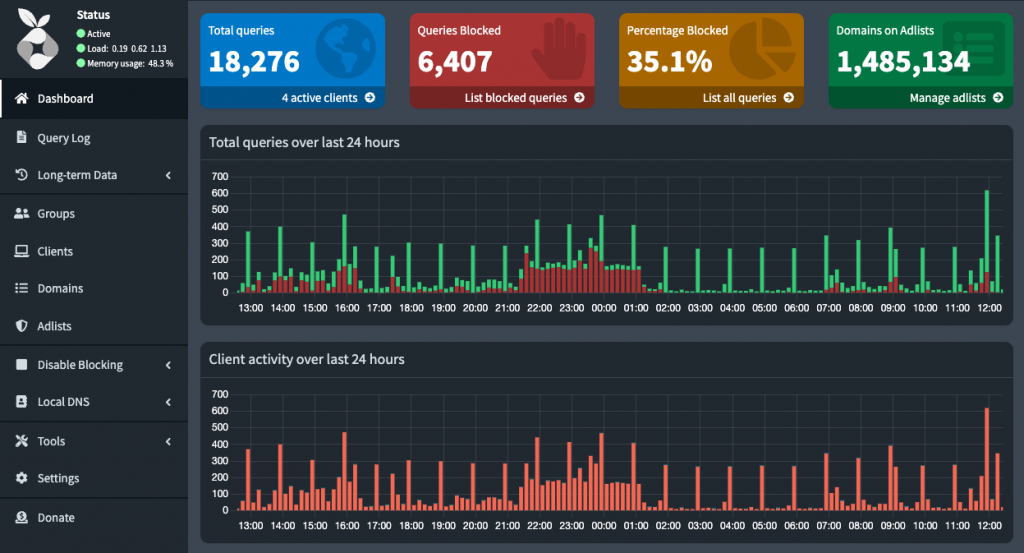
Using Pi-hole from the VPN clients
To use the Pi-hole hosted in the same VPN server from the VPN clients, you can specify a DNS property in the client config, i.e. if the server is 100.100.1.1 and the client is 100.100.1.2:
[Interface]
PrivateKey = <client-private-key>
Address = 100.100.1.2/32
DNS = 100.100.1.1
[Peer]
PublicKey = <server-public-key>
PresharedKey = <preshared-key>
Endpoint = <my-home-server>:51820
AllowedIPs = 0.0.0.0/0, ::/0
PersistentKeepalive = 25Every time that you connect the VPN, the DNS server in the client changes to 100.100.1.1 and it is reverted to the previous DNS server when the VPN is disconnected.
Additionally, Pi-hole needs to be listening in the wg0 interface, I explained how to make Pi-hole listen on multiple interfaces in the Pi-hole post.